Sales & Marketing Report 2017: Taking the Risk Out of Digitization
The inherent complexity and “length” of global supply chains, along with a dramatic increase in the volume and variety of data exchanged between suppliers, manufacturers and customers, is raising the profile and importance of securing this data.
Furthermore, as cloud, or hosted, business applications grow in usage, the potential to “expose” data to unauthorized users also grows. Indeed, within the consumer goods supply chain, cyber security has now passed physical security as the major concern for many companies.
This does not mean, of course, that physical security issues are not still important, just that the number of cyber attacks have increased to the point where companies must focus more on them. How consumer goods manufacturers approach security, and the tools they use in combatting both physical and virtual breaches, is a huge IT focus as we move through 2017.
Indeed, cyber security is a key element in two of the main drivers of change for the industry:
Information as an Asset: Increasing the use, analysis, and security of information. IDC estimates that the digital universe is growing at 40% per year and will reach 44ZB, or 44 trillion gigabytes, by 2020. The challenge is to exploit information as an asset that can fuel digital transformation — to create new efficiencies or generate new revenue streams. Consumer goods manufacturers are recognizing that their information must be usable for analysis and, in turn, analyzed.
This will allow them to better understand their products and processes with visibility into the actual performance, as well as to create a foundation for continuous improvement and new products and services. Ensuring that data is gathered and analyzed in a cost-effective manner, and protecting this information as it’s collected, stored and analyzed, is critical.
Business-Relevant Security: Connecting cyber and physical security across IT and OT. Although the IT organizations of consumer goods manufacturers can usually identify what they need for a complete cyber security strategy, the increasing overlap of IT and OT (operations technology) is redefining their security requirements in terms of tools, technologies, policies and governance.
In addition to securing data centers, networks, transactional systems, customer data, and engineering designs, the convergence of IT and OT, and the addition of sensor data on connected assets, products, and supply chains, are changing the security roadmap. An integrated approach to security will also account for sensors, supervisory control and data acquisition (SCADA), GIS, GPS, and data historians.
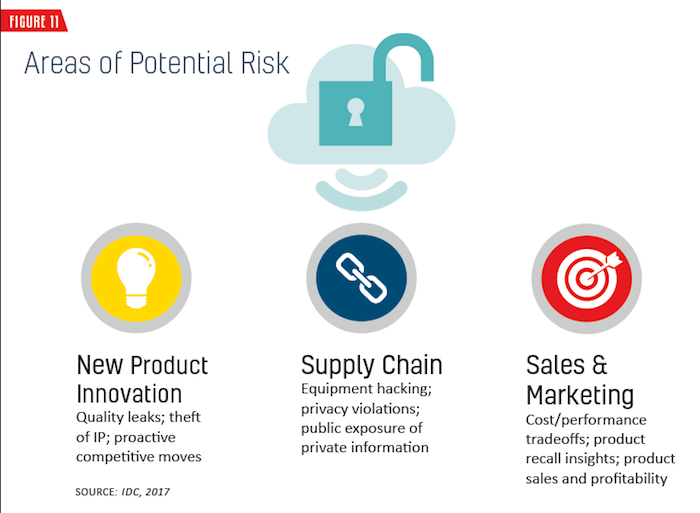
These may seem like overly technical points, but they are highly relevant to the sales and marketing functions because data and insights are increasingly becoming part of what these businesses sell. Under Armour, for example, is increasingly viewing itself as a health data company that happens to sell clothing. The ability for Under Armour to sell consumer “experiences” based on the data collected from sensor-enabled apparel is related absolutely to the accuracy and security of their data. Figure 11 illustrates areas of potential risk.
_____________________________________________
To read the rest of the report, click on the links below:
- Sales & Marketing Report 2017: Editor's Note
- The Progress Report
- The Evolving Role of TPM
- What to Do with Data
- Is DTC the Future — or the Present?
- Taking the Risk Out of Digitization
- Building a Smart Digital Enterprise
To download the full report, click here.
